Cisco Vpn Client For Mac 10.12
Posted By admin On 02.02.19Cisco VPN Client allows you to establish encrypted VPN tunnels for highly secure remote connectivity for your mobile employees or teleworkers. Simple to deploy and use, our IP Security (IPsec)-based VPN Client is compatible with all Cisco VPN products.
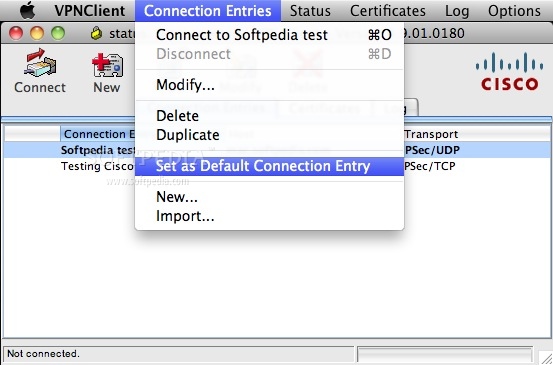
Cisco Anyconnect Vpn Client Download
Have troubles with connecting to my VPN from Mac. Using default Mac client, pre-shared secret. Also this works well on iOS 10.3.2 from the same Wi-Fi network. Firewall is disable, no Little Snitch. MacOS error message says 'The L2TP-VPN server did not respond' Also, I've tried to connect open free VPN, us.freel2tpvpn.com and got no response again, so I think it's a macOS problem, not the server / routing. Do you have any ideas? Here is my /var/log/ppp.log Tue Jun 13 15:: publish_entry SCDSet() failed: Success!
Download Cisco Vpn Client For Mac
Cisco recently released their new AnyConnect Secure Mobility Client Version 4.3.03086. This new version is compatible with Mac OS X 10.9 and higher (including the latest version of Mac OS X 10.12 Sierra). Cisco vpn client windows 10 free download - Cisco VPN Client Fix for Windows 8.1 and 10, Netlock VPN Client for Cisco, VPN Client, and many more programs. Best Video Software for the Mac How To.
Tue Jun 13 15:: publish_entry SCDSet() failed: Success! Tightvncserver client for mac. Tue Jun 13 15:: l2tp_get_router_address Tue Jun 13 15:: l2tp_get_router_address 172.16.21.1 from dict 1 Tue Jun 13 15:: L2TP connecting to server '86.102.88.210' (86.102.88.210). Tue Jun 13 15:: IPSec connection started Tue Jun 13 15:: IPSec connection failed update 1 checked udp ports 500, 1701, 4500 — all open from mac update 2 set up another l2tp ipsec preshered secret server on windows and got same result — don't respond on mac, connected on iphone update 3 wiresharked booth on 'connections', and there is no udp packets from mac on connection, but test packets are ok. Definitely the mac vpn client is broken (firewall is off), where should I dig? First step: Ensure that outgoing L2TP connections work properly. To do that, run the following commands in Terminal (you can copy and paste if you want): /usr/bin/nc -uvw5 portquiz.net 500 /usr/bin/nc -uvw5 portquiz.net 1701 /usr/bin/nc -uvw5 portquiz.net 4500 You should get something that looks like this (note the three 'succeeded' lines): found 0 associations found 1 connections: 1: flags=82 outif en0 src 192.168.1.2 port 56916 dst 178.33.250.62 port 500 rank info not available TCP aux info available Connection to portquiz.net port 500 [tcp/isakmp] succeeded! Found 0 associations found 1 connections: 1: flags=82 outif en0 src 192.168.1.2 port 56917 dst 178.33.250.62 port 1701 rank info not available TCP aux info available Connection to portquiz.net port 1701 [tcp/l2f] succeeded!